Install Acunetix Linux

Grabber is a web application scanner. Basically it detects some kind of vulnerabilities in your website. Grabber is simple, not fast but portable and really adaptable. This software is designed to scan small websites such as personals, forums etc. absolutely not big application: it would take too long time and flood your network.
Acunetix is available only for Windows Platform. You can try your luck by installing it using playonlinux. But there are other alternatives to. Open office is a wonderful alternate of MS office, the easiest way to install open office is by using terminal and command “apt-get install openoffice.org” but one of our user has discussed about the repositories problem in Kali Linux. We have also seen that the debain repositories is not working properly hence you cannot install packages.
Disclaimer – Our tutorials are designed to aid aspiring pen testers/security enthusiasts in learning new skills, we only recommend that you test this tutorial on a system that belongs to YOU. We do not accept responsibility for anyone who thinks it’s a good idea to try to use this to attempt to hack systems that do not belong to you
Why this kind of application ?
This is a very small application (currently 2.5kLOC in Python) and the first reason of this scanner is to have a “minimum bar” scanner for the Samate Tool Evaluation Program at NIST.
Grabber is also for me a nice way to do some automatics verification on websites/scripts I do. Users should know some things about web vulnerabilities before using this soft because it only tell you what vulnerability it is… not how to solve it.
Current features
Because it’s a small tool, the set of vulnerabilities is small…
- Cross-Site Scripting
- SQL Injection (there is also a special Blind SQL Injection module)
- File Inclusion
- Backup files check
- Simple AJAX check (parse every JavaScript and get the URL and try to get the parameters)
- Hybrid analysis/Crystal ball testing for PHP application using PHP-SAT
- JavaScript source code analyzer: Evaluation of the quality/correctness of the JavaScript with JavaScript Lint
- Generation of a file [session_id, time(t)] for next stats analysis.
Does it scan the JavaScript ?
Yes! It can handle the JavaScript files, parse it to retrieve the server sides scripts names and try to get some parameters name…
This application is based on:
- Researchs from famous websites/guys:
- ha.ckers.org (the XSS vector at least)
- SPI-Dynamics lab/portal
- OWASP etc.
- and a huge amount of information given by lots of tools (Pantera, Paros, Wapiti, WebInspect, Hailstorm, AppScan etc.)
- Python:
Grabber aim to be simple. It’s a small tool, does not provide any GUI or PDF report! There is XML reports (you can easily create a XSLT to render the XML for you manager).
Grabber usage
Spider the web application to a depth of 1 (–spider 1) and attempt SQL (–sql) and XSS (–xss) attacks at the given URL (–url http://kali-test-random-gen.com):
#####################################
CEWL (pronounced “cool” ) is a custom word list generator written in Ruby that with a given URL and a specified depth and possibly external links , returns a list of words that can then be used for application bruteforce as john or hydra , it was written by Digininja .
Disclaimer – Our tutorials are designed to aid aspiring pen testers/security enthusiasts in learning new skills, we only recommend that you test this tutorial on a system that belongs to YOU. We do not accept responsibility for anyone who thinks it’s a good idea to try to use this to attempt to hack systems that do not belong to you
Installation
CEWL is pre- installed on Kali linux but if you use a minimal version, it is available in the repositories ,
apt-get install cewl
using cwel
The cwel syntax is: $ CEWL [OPTION] … URL , and the options are:
–help or -h for options ,
–keep or -k to keep the downloaded files ,
–depth <x> or -d <x> for depth (default 2)
–min_word_length <length> , -m <length> for the minimum length of words (default 3)
–offsite or -o let depth visit another site.
–write <file> , -w <file> references the result in a file,
–ua <user- agent > or -u <user- agent > specifies the user agent ,
-n –no -words or does not display the output result ,
–meta or -a included meta data and –meta_file < file > to write them to an output file ,
–email , -e included email addresses ,
–meta – temp- dir <directory> the temporary directory used by exiftool during parsing (default / tmp ) , and -v for verbosity .
This help is displayed with the –help
cewl –help
Here is an example to create a minimum of 4 letters password file from the home page of a site and save it in a text file with the following command .
cewl.rb -w passwords.txt http://www.site.com
After a few minutes you will get a dictionary file.
###########################
Metasploit Best Hacking Tools Of 2016
Rather than calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can utilize to build your own custom tools. This free tool is one of the most popular cybersecurity tool around that allows you to locate vulnerabilities at different platforms. Metasploit is backed by more than 200,000 users and contributors that help you to get insights and uncover the weaknesses in your system.
This top hacking tool package of 2016 lets you simulate real-world attacks to tell you about the weak points and finds them. As a penetration tester, it pin points the vulnerabilities with Nexpose closed–loop integration using Top Remediation reports. Using the open source Metasploit framework, users can build their own tools and take the best out of this multi-purpose hacking tool.
Metasploit is available for all major platforms including Windows, Linux, and OS X.
Get IT Security & Ethical Hacking Certification Training Course at fossBytes.
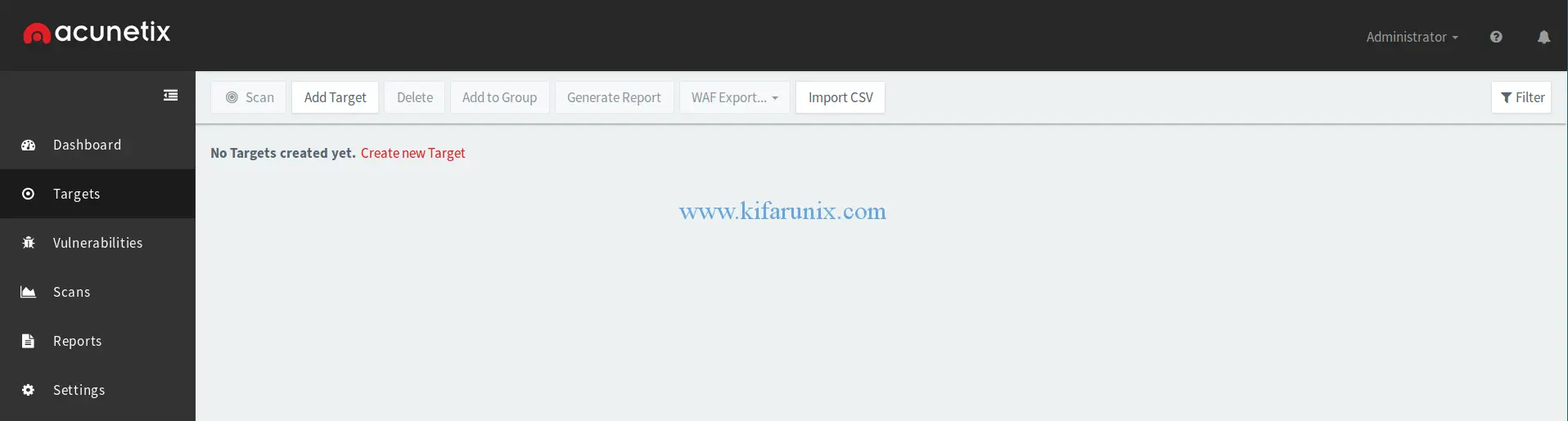
Acunetix WVS Best Hacking Tools Of 2016
Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. This multi-threaded tool crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities. This fast and easy to use tool scans WordPress websites form more than 1200 vulnerabilities in WordPress.
Acunetix comes with a Login Sequence Recorder that allows one to access the password protected areas of websites. The new AcuSensor technology used in this tool allows you to reduce the false positive rate. Such features have made Acunetix WVS a preferred hacking tools that you need to check out in 2016.
Acunetix is available for Windows XP and higher.
Nmap Best Hacking Tools Of 2016
Nmap – also known as Network Mapper – falls in the category of a port scanner tool. This free and open source tool is the most popular port scanning tool around that allows efficient network discovery and security auditing. Used for a wide range of services, Nmap uses raw IP packets to determine the hosts available on a network, their services along with details, operating systems used by hosts, the type of firewall used, and other information.
Last year, Nmap won multiple security products of the year awards and was featured in multiple movies including The Matrix Reloaded, Die Hard 4, and others. Available in the command line, Nmap executable also comes in an advanced GUI avatar.
Nmap is available for all major platforms including Windows, Linux, and OS X.
Read more here and find download link.
Wireshark Best Hacking Tools Of 2016
Wireshark is a well-known packet crafting tool that discovers vulnerability within a network and probes firewall rule-sets. Used by thousands of security professionals to analyze networks and live pocket capturing and deep scanning of hundreds of protocols. Wireshark helps you to read live data from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others.
This free and open source tool was originally named Ethereal. Wireshark also comes in a command-line version called TShark.
This GTK+-based network protocol analyzer runs with ease on Linux, Windows, and OS X.
Read more here and find download link.
oclHashcat Best Hacking Tools Of 2016
If password cracking is something you do on daily basis, you might be aware of the free password cracking tool Hashcat. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of your GPU.
oclHashcat calls itself world’s fastest password cracking tool with world’s first and only GPGPU based engine. For using the tool, NVIDIA users require ForceWare 346.59 or later and AMD users require Catalyst 15.7 or later.
This tool employs following attack modes for cracking:
- Straight
- Combination
- Brute-force
- Hybrid dictionary + mask
- Hybrid mask + dictionary
Mentioning another major feature, oclHashcat is an open source tool under MIT license that allows an easy integration or packaging of the common Linux distros.
This useful hacking tool can be downloaded in different versions for Linux, OSX, and Windows.
Nessus Vulnerability Scanner Best Hacking Tools Of 2016
This top free hacking tool of 2016 works with the help of a client-server framework. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. Nessus serves different purposes to different types of users – Nessus Home, Nessus Professional, Nessus Manager and Nessus Cloud.
Using Nessus, one can scan multiple types of vulnerabilities that include remote access flaw detection, misconfiguration alert, denial of services against TCP/IP stack, preparation of PCI DSS audits, malware detection, sensitive data searches etc. To launch a dictionary attack, Nessus can also call a popular tool Hydra externally.
Apart from the above mentioned basic functionalities, Nessus could be used to scan multiple networks on IPv4, IPv6 and hybrid networks. You can set scheduled scan to run at your chosen time and re-scan all or a subsection of previously scanned hosts using selective host re-scanning.
Nessus is supported by a variety of platforms including Windows 7 and 8, Mac OS X, and popular Linux distros like Debian, Ubuntu, Kali Linux etc.
Maltego Best Hacking Tools Of 2016
Maltego is an open source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you. Maltego excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment.
Maltego is a great hacker tool that analyzes the real world links between people, companies, websites, domains, DNS names, IP addresses, documents and whatnot. Based on Java, this tool runs in an easy-to-use graphical interface with lost customization options while scanning.
Maltego hacking tool is available for Windows, Mac, and Linux.
Social-Engineer Toolkit Best Hacking Tools Of 2016
Also featured on Mr. Robot, TrustedSec’s Social-Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. On the show, Elliot is seen using the SMS spoofing tool from the Social-Engineer Toolkit.
This Python-driven tool is the standard tool for social-engineering penetration tests with more than two million downloads. It automates the attacks and generates disguising emails, malicious web pages and more.
To download SET on Linux, type the following command:
git clonehttps://github.com/trustedsec/social-engineer-toolkit/ set/ |
Apart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows.
Other top hacking tools in multiple categories:
Web Vulnerability Scanners – Burp Suite, Firebug, AppScan, OWASP Zed, Paros Proxy
Vulnerability Exploitation Tools – Netsparker, sqlmap, Core Impact, WebGoat, BeEF
Forensic Tools – Helix3 Pro, EnCase, Autopsy
Port Scanners – Unicornscan, NetScanTools, Angry IP Scanner
Traffic Monitoring Tools – Nagios, Ntop, Splunk, Ngrep, Argus
Debuggers – IDA Pro, WinDbg, Immunity Debugger, GDB
Rootkit Detectors – DumpSec, Tripwire, HijackThis
Encryption Tools – KeePass, OpenSSL, OpenSSH/PuTTY/SSH, Tor
Password Crackers – John the Ripper, Aircrack, Hydra, ophcrack
We hope that you found this top hacking tools of 2016 list helpful. Share your reviews in the comments below and help us improve this list.
###############################
The goal of Xplico is extract from an internet traffic capture the applications data contained.
For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico isn’t a network protocol analyzer. Xplico is an open source Network Forensic Analysis Tool (NFAT).
Xplico is released under the GNU General Public License and with some scripts under Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported (CC BY-NC-SA 3.0) License. For more details seeLicense.
Disclaimer – Our tutorials are designed to aid aspiring pen testers/security enthusiasts in learning new skills, we only recommend that you test this tutorial on a system that belongs to YOU. We do not accept responsibility for anyone who thinks it’s a good idea to try to use this to attempt to hack systems that do not belong to you
instalation
to instal xplico open a new terminal ans type
apt-get install xplico
using xplico
to use xplico open your web browser and type http://localhost:9876
If xplico was not started :
open a new terminal and type service xplico start
open your browser and logg in as admin , you will see a webpage like that
sellect new case , type case name then creat
then sellect that case
then select new session
name a session and click creat
and you will get a webpage like that
now we gonna launch “ettercap” to start capturing traffic
open a new terminal and type ettercap -G
now we gonna select unified sniffing
here we need to chose our network interface and then click OK
now we gonna make a scan for hosts
now we have all hostes in our local network, next we need to chose a target to do that just select an ip address and click Add to target 1 also we can add more than one target .
in this tutorial im gonna select a windows xp machine as a target
select mitm and click ok to launch that
and then start sniffing
now we are enable to sniff traffic going between the systeme and our gateway
now we go back to xplico select eth0 interface and click start
then we move over to our windows xp machine and go to internet explorer and search for exempel for cats as we can see here
then go back to our kali linux machine and click stop sniffing
browse through between data collected on that traffic graphs,web, mail,chat ….
we can show the google traffic
and if we select images we can see all images traffic
############################
People hear in the news everyday that some website was attacked using DOS, well DOS is not Disk Operating System it is much bigger it can bring an entire website down even it has huge scale servers.
Here I would like to share a basic program using RMI based bots that will be helpful for research purpose only. My intention is not to encourage script kiddies but just to give an idea of some of the things that can be achieved using RMI in JAVA.
First we have created an interface that will be concreted in it’s implementation later. But, the main purpose behind creating this interface is just for RMI as the look up functionality of RMI needs an interface instead of complete implementation.
Later I have Imported the necessary imports to make the implementations of the interface
“Disclaimer – Our tutorials are designed to aid aspiring pen testers/security enthusiasts in learning new skills, we only recommend that you test this tutorial on a system that belongs to YOU. We do not accept responsibility for anyone who thinks it’s a good idea to try to use this to attempt to hack systems that do not belong to you”
Now this time is just to provide an implementation of that interface:
The UnicastremoteObject is to implement the remote server in the clinets and servers system hence the attack is a ddos, I have also inherited the interface DDOSService in the previous code snippet which in turns it inherits the Remote package.
Followed by it we create a server Instance in order to start the attack we are shooting the server with a http request we throw a exception if there is error in the code or a priority is out of number.
Till now we have almost done with our Server side code which we will be executing at our control panel machine from where we will be able to provide service to all those clients that will be waiting for our command. Actually here we have used RMI in reverse order as the clients are just acquiring the name of target machine from server. And once they got the name they start hitting it from their own machines.
As this code is just a day effort so probably need some further improvement too.
Now finally, we are at a stage to write the client side code that will be performing the actual task of sending fake requests to the client.
But in RMI we just need to compile in a bit different way. As it’s related to client-server communication so we must need a stub that will be used as a communication bridge in between client and a server.
Once we are done with the server we need to work on the client side hence it is a DDOS (Distrubuted Denial of the Service attack) we generate exceptions in the case of connectivity issues otherwise there is an infinite loop that hits the server we can make it better by using Multi-Threading it will cause more damage hey,I am not the one showing that to you but I will give you a
Hint : Inherit the Thread Class from another class and make the shift the entire code to a method in the Thread class and now you know what to do or refer this article.
When we are already done with the coding. So, now we need to compile and test it.
javac DDOSServiceClient.java
javac DDOSServiceServer.java
rmic DDOSServiceServer
start rmiregistry
java DDOSServiceServer on server machine
java DDOSServiceClient on client machine.
#########################
So What Can You Do When You Clone SIM card ?
Well There are many things to do when you clone a SIM Card, You can secretly spy on the victims calls and data transfers, make him mobile bill go crazy, send messages and make calls from his number, All without touching the victims Cell Phone.
First A Little Knowledge Of SIM Hacking :
Not every SIM Card is clone-able, There are two types of SIM Card :
COMP128v1: The most popular and clone-able version of SIM Cards, Distributed widely till 2004 in USA (2007 In ASIA Countries), Of the number of victim is older than 2004 in USA or 2007 in Asia, Chances are you can clone it pretty easily.
COMP128v2: The newer SIM's, Capable of better 3G Reception, Video Call Support, New and Secure firmware, Complex Design, Very ( I mean very fu*king very) Hard. If the SIM is bought after 2004, it is probably this version.
Things Required :
So The inventory is full, Lets Begin The Work :
The Step 1 :
Step 2 :
Step 3 :
First Run The IMSI Search :
| Note Down The IMSI Number ! |
Write down the ICC Number too, Now run the KI Search, This may take some time :
| After 45 Minutes, IF you don't Get the First Value, The Sim IS Un-cloneable ! |
Now remove the Vic's SIM And give it back to him.
Step 4 :
Step 5 :
| The Setup Menu |
Step 6 :
| Wait For The Conformation, Then Select OK. |
A write EEPROM file window will appear. Name the EEPROM file SuperSIM_EP.HEX and click the Save button.
| Now You Have 2 Files, Ready to be Flashed. |
Step 7 :
| Flashing The Blank SIM. |
Step 8 :
| Congrats, You Have Cloned A SIM Card ! |
So here you have it, A Cloned SIM Card, Now when somebody calls the victim, Both of the mobiles will ring, same will happen in the case of SMS, But only one can pick up the call. Also don't do something big that will raise a red flag in Mobile Company. You are responsible for your actions.
Arcon Evo & 3D Architect support includes Technical, Installation & Activation support for 12 months via email plus access to our web based tutorials and forums. We aim to respond as soon as possible subject to support query and availability. Powerful, flexible 2D & 3D home design CAD Software. Arcon Evo is CAD software for building design and floor plan requirements. Arcon Evo is the most flexible design package Elecosoft provides offering an extensive range of CAD tools for all aspects of building design including residential and large scale developments. Get the brochure. 3d architect home designer pro.